The United Kingdom's National Risk Register - 2023 Edition
Emergency Planning
AUGUST 3, 2023
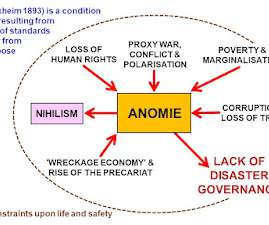
The new version presents 89 major hazards and threats that could potentially disrupt life in the United Kingdom and possibly cause casualties and damage. It explains its own rationale and presents the 89 'risks' one by one. The 2023 NRR is clear and concise.
















































Let's personalize your content