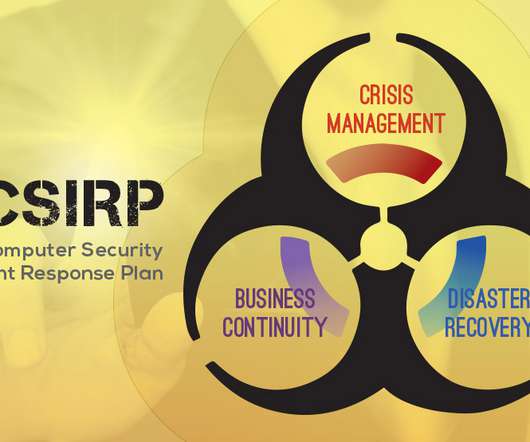
Cyber Incident Response Plans – Turning Words into Action
Bernstein Crisis Management
FEBRUARY 11, 2021
Yet surprisingly few have meaningful and up-to-date incident response plans (IRPs) in place to manage and mitigate this threat. Such plans, if properly designed and updated, can spell the difference between strong mitigation and recovery from an incident and prolonged, crisis-driven recovery or no recovery at all.














































Let's personalize your content