Aligning Cyber Incident Response Planning with Your BC/DR Program
eBRP
JANUARY 10, 2019
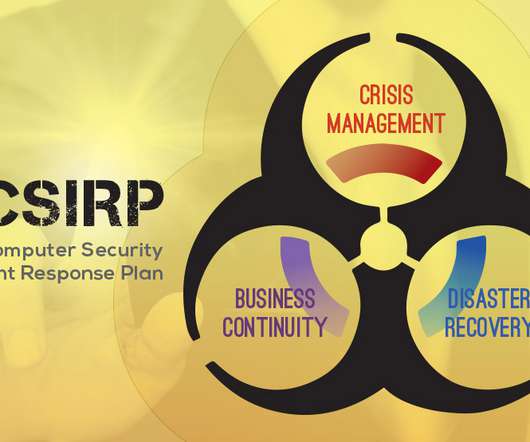
In the IT realm, CIO’s and CISO’s now focus their efforts on mitigating those risks, and planning responses to potential data breaches, malware and other cyber threats. You can view the webinar on demand here. After you have watched the webinar, we invite your feedback. Please contact us at info@eBRP.net.












Let's personalize your content