Can Your Disaster Recovery Keep Up? Part 1 – The Need for Speed
Zerto
FEBRUARY 25, 2025
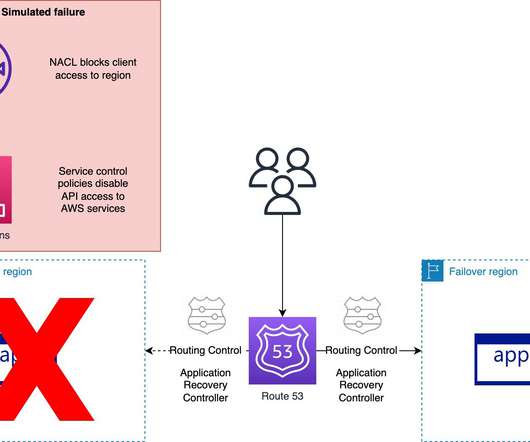
Weve all been there: watching the dreaded spinning wheel during the climax of a video, stuck at an airport gate as flight delays ripple across the screens, or worse, during an emergency, facing system outages when we need them most. Simplifying failover: Our automated processes reduce complexity so you can focus on getting back to business.























Let's personalize your content