How to defuse a bomb on a spaceship
Crisis Response Journal
JUNE 22, 2021
The world is a spaceship travelling around the sun, but inside the air is getting stuffy and the crew are growing in number.

Crisis Response Journal
JUNE 22, 2021
The world is a spaceship travelling around the sun, but inside the air is getting stuffy and the crew are growing in number.

Disaster Zone Podcast
JUNE 22, 2021
While climate change and disasters are mentioned frequently in the popular media, most of the information being shared is about climate mitigation that has to do with reducing the amount of carbon being emitted into the atmosphere. There is little discussion of climate adaptation. This podcast looks specifically at adaption as a strategy that can be implemented now and can provide immediate results to reduce climate related damages.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

KingsBridge BCP
JUNE 22, 2021
Business Continuity Profile. It’s one thing to have a business continuity plan, but it’s another to make sure your staff know about it. Those involved in writing the plan and the core members of recovery teams are likely aware of the plan. This is great, but what about everyone else in the organization? When bad things happen, will the staff know the company has a plan in place?

Donyati
JUNE 21, 2021
As organizations around the globe begin to negotiate a new array of post-Covid situations – such as when, or if, to return employees to the office – some celebration is certainly in order. But although 2020’s pandemic is finally ending, a new era for Business Continuity Planning (BCP) has just begun, according to Donyati BCP experts Joseph Brewer and Patrick Dunn.

Speaker: Erroll Amacker
As businesses increasingly adopt automation, finance leaders must navigate the delicate balance between technology and human expertise. This webinar explores the critical role of human oversight in accounts payable (AP) automation and how a people-centric approach can drive better financial performance. Join us for an insightful discussion on how integrating human expertise into automated workflows enhances decision-making, reduces fraud risks, strengthens vendor relationships, and accelerates R

Crisis Response Journal
JUNE 23, 2021
Lina Kolesnikova investigates the phenomenon of bystanders filming and taking photos of accident victims rather than calling the emergency services for help, or clearing the way for first responders
Continuity Professional Pulse brings together the best content for business continuity professionals from the widest variety of industry thought leaders.
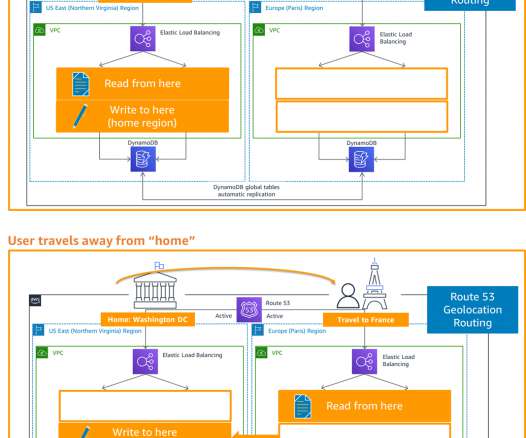
AWS Disaster Recovery
JUNE 23, 2021
In my first blog post of this series , I introduced you to four strategies for disaster recovery (DR). My subsequent posts shared details on the backup and restore , pilot light, and warm standby active/passive strategies. In this post, you’ll learn how to implement an active/active strategy to run your workload and serve requests in two or more distinct sites.

LogisManager
JUNE 24, 2021
Looking Around the Corner: Why Is ESG Important In The Present And Future. By Steven Minsky. Introduction: Why is ESG important? The topic of environmental, social and governance (ESG) criteria is especially prominent right now. But why is ESG important? It’s all about the See-Through Economy. By taking a look at trends and patterns over the course of recent history, it’s clear that ESG is a growing concern for consumers, investors and regulators everywhere.

Crisis Response Journal
JUNE 24, 2021
Lyzi G Cota introduces the first in a series of blogs that explore the importance of accounting for livestock and poultry during a crisis

FEI
JUNE 23, 2021
I often lead crisis management drills for one of our customers in the hospitality industry. One of their biggest concerns is how to effectively recover from their loss of staff during COVID-19. It wasn’t just small business that took a major hit during the pandemic. Some big-name franchises did as well. All this leads to the question: How do you continue to respond to crises with a skeleton staff?

Advertisement
During a crisis, successful organizations are led by strong leaders who communicate continuously with all stakeholders and have plans that are flexible enough to allow changes to be made on the fly. What You'll Learn: Understanding the characteristics of actionable business continuity plans. Step-by-step guidance on building robust and adaptable BCPs.

Advancing Analytics
JUNE 22, 2021
To Make An Impact In Your Business By Gavita Regunath and Dan Lantos “The goal of forecasting is not to predict the future but to tell you what you need to know to take meaningful action in the present.” — Paul Saffo This article aims to provide a general overview into time series forecasting, the top time series algorithms that have been widely used to solve problems, followed by how to go about choosing the right forecasting algorithm to solve a specific problem.

BCM METRICS
JUNE 24, 2021
It’s one thing to talk about crisis management as it affects other people’s organizations. It’s something else when it involves your college-age son and he’s seriously ill in a country 6,000 miles away. Read for more on how this family crisis reenforced my crisis management training and experience. When Crisis Hits Home I provide crisis management advice to organizations for a living. […].

Plan B Consulting
JUNE 24, 2021
In this week’s bulletin, I discuss the idea of a hypercomplex world and preparing for different scenarios in it. A few weeks ago, I wrote a bulletin on scenario planning and how under the new requirement of Operational Resilience for FCA and PRA, regulated organisations now have a requirement to determine ‘extreme but plausible scenarios’ to see if they would continue delivering their services if the said scenario occurred.
Assurance IT
JUNE 24, 2021
What is a Multi-Factor Authentication? Multi-factor authentication (MFA) is a method of protecting your online identity. It’s used to verify that the user is who they say they are. By doing so, the MFA asks the user to provide two forms of identification or confirmation that they are who they say they are. These pieces of identification fall into three categories: something they are, something they know, and something they have.

Speaker: Tim Buteyn, President of ThinkingKap Learning Solutions
Join this brand new webinar with Tim Buteyn to learn how you can master the art of remote onboarding! By the end of this session, you'll understand how to: Craft a Tailored Onboarding Checklist 📝 Develop a comprehensive, customized checklist that ensures every new hire has a smooth transition into your company, no matter where they are in the world.

Alert Media
JUNE 24, 2021
The post 4 Steps To Performing a Business Impact Analysis appeared first on AlertMedia.

Security Industry Association
JUNE 23, 2021
AcceleRISE – hosted by SIA’s RISE community – is an essential experience for tomorrow’s security leaders taking place virtually Aug. 23-25. SILVER SPRING, Md. – The Security Industry Association (SIA) has announced the 2021 agenda and speaker lineup for AcceleRISE: The Challenge , an essential experience hosted by SIA’s RISE community for young professionals in the security industry.

Plan B Consulting
JUNE 24, 2021
In this week’s bulletin, I discuss the idea of a hypercomplex world and preparing for different scenarios in it. A few weeks ago, I wrote a bulletin on scenario planning and how under the new requirement of Operational Resilience for FCA and PRA, regulated organisations now have a requirement to determine ‘extreme but plausible scenarios’ to see if they would continue delivering their services if the said scenario occurred.

Assurance IT
JUNE 22, 2021
Did you know that in 2020, over 18,000 vulnerabilities were created? When your computer is linked to an insecure network your software security can be compromised. This happens without proper protocols in place. Updates that are forgotten, product flaws, and unresolved developer issues expose your clients to computer security risks. All of this is vulnerabilities in your enterprises’ software security.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Alert Media
JUNE 22, 2021
The post How AlertMedia Customers Utilize Real-Time Intelligence to Protect Their People and Business appeared first on AlertMedia.

Security Industry Association
JUNE 22, 2021
The publication is designed to help security technology companies enhance their management of personal information. . SILVER SPRING, Md. – The Security Industry Association (SIA) has released its new Privacy Code of Conduct , a resource designed to guide security technology companies in implementing privacy programs and protecting personal data. The document was created by SIA’s Data Privacy Advisory Board, a group of SIA members that produces resources and events aimed at promoting a better

Behavior Group
JUNE 22, 2021
I read with interest the latest batch of evaluation data from MITRE on various endpoint solutions, this time focusing on the detect, response and containment of these various solutions against malware created by FIN7 and CARBANAK threat groups. While academically interesting, it illustrates the difficulty in giving reviews to cybersecurity products in the endpoint protection… Continue reading.

CIO Governance
JUNE 21, 2021
The Certified Information Systems Auditor (CISA) certification validates your knowledge for information systems auditing, assurance, control, security, cybersecurity, and governance. Offered by the Information Systems Audit and Control Association (ISACA), the credential is designed for IT and IS auditors tasked with evaluating an organization’s information systems to identify issues and potential security threats.

Advertisement
The Complete Guide to Mastering Business Continuity is a step-by-step resource for developing an effective Business Continuity Management (BCM) program and navigating challenges. Whether building from scratch or enhancing a plan, this guide offers practical tools, expert advice, and strategies to ensure resilience. What You’ll Learn: Key elements of BCM and resiliency Steps to build and test your Business Continuity Plan (BCP) Conducting risk assessments and BIAs Integrating cybersecurity into p
VOX Veritas
JUNE 24, 2021
With InfoScale, you can seamlessly integrate on-premises resources and public cloud services as part of a distributed cloud strategy that enables you to run your IT services on any platform.

Security Industry Association
JUNE 22, 2021
Become a donor – Join leading companies who have demonstrated outstanding commitment to progress in the security industry. SILVER SPRING, Md. – The Security Industry Association (SIA) has announced that the deadline to apply for the 2021 SIA Women in Security Forum Scholarship has been extended to Wednesday, June 30. Open to both men and women who work for SIA member companies, the SIA Women in Security Forum Scholarship is designed to further educational opportunities and promote advancement fo

Business Continuity Today
JUNE 22, 2021
Like many people, I've sorely missed going to sporting events last year there were games, however, cardboard cutouts (that were kind of strange) and piped-in crowd noises were the norms in light of the world's COVID-19 pandemic. And also like many —while I understand the need for and support precautions to protect ourselves and others from the virus and mitigate its spread, I've been longing to enjoy the electric feel of a live sporting event.

Prism International
JUNE 22, 2021
Guest Article By: Joshua D. Hundeby-DeVries, CSDS. Editor’s Note: In light of current market dynamics, where many clients now find their employees working from home, it seems appropriate to revisit the topic of Residential Shred Bags. A service provider who was already effectively leveraging them in their business model originally wrote this article in 2018.

Speaker: Tim Buteyn, President of ThinkingKap Learning Solutions
💢 Do you find yourself stuck in never-ending review cycles? Are you wondering if your Subject Matter Expert actually got that last review request? Are you having trouble trying to decipher impractical or conflicting feedback? 💢 If any of these scenarios sounds familiar, you may benefit from a crash course on managing SME relationships!

Plan B Consulting
JUNE 24, 2021
This week I take a look at the BrewDog crisis communications, including how well they handled accusations against them and how your company can use the lessons learnt. I am partial to a Punk IPA and some of the company’s rather gooseberry tasting beers. So I thought now that the incident is out of the news, I would write about BrewDog’s crisis communications after an open letter from existing and former employees “Punks With Purpose” alleging a toxic culture for employees within the company was

Security Industry Association
JUNE 21, 2021
Pete O’Dell, CEO, Swan Island Networks. New Security Industry Association (SIA) member Swan Island Networks is a software-as-a-service company that delivers trusted situational awareness and threat intelligence services. The company is headquartered in Portland, Oregon. SIA spoke with Swan Island Networks CEO Pete O’Dell about the company, the security industry and working with SIA.

Business Continuity Today
JUNE 22, 2021
Like many people, I've sorely missed going to sporting events last year there were games, however, cardboard cutouts (that were kind of strange) and piped-in crowd noises were the norms in light of the world's COVID-19 pandemic. And also like many —while I understand the need for and support precautions to protect ourselves and others from the virus and mitigate its spread, I've been longing to enjoy the electric feel of a live sporting event.
Let's personalize your content