Disaster Recovery & Business Continuity Up & Comer: Nuveric’s PetaGys Powered by Oracle’s Solaris
ChannelBloom
FEBRUARY 27, 2018
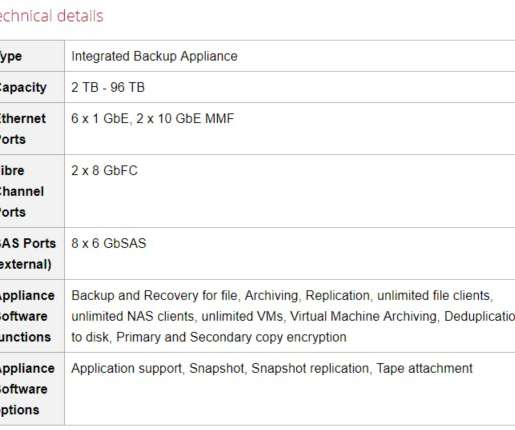
The PetaGys Powered by Oracle Solaris integrates correctly-sized hardware and data protection software into a complete onsite backup, offsite cloud, and business continuance solution. The appliance enables a fast and hassle-free setup of a comprehensive disaster recovery environment. The all-in-one solution fits perfectly for midsize IT environments with a strong support of virtualization.



































Let's personalize your content