Protecting Houses of Worship
Recovery Diva
SEPTEMBER 11, 2024
From FEMA: a series of sessions on Protecting House of Worship

Recovery Diva
SEPTEMBER 11, 2024
From FEMA: a series of sessions on Protecting House of Worship

BryghtPath
SEPTEMBER 11, 2024
Explore essential strategies for ensuring seamless customer support during disruptions. Understand why Business Continuity for Customer Service is crucial for retaining customers, enhancing brand reputation, and navigating uncertainty in today's business landscape. The post Ensuring Business Continuity for Customer Service Success appeared first on Bryghtpath.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Rand Blog
SEPTEMBER 11, 2024
Housing is front and center in both of the major parties' campaigns for the White House. We asked two RAND experts to bring us up to speed the housing issues and discuss the policies and proposals that might ease the historically tight housing market for buyers and renters alike.

Pure Storage
SEPTEMBER 11, 2024
From Hurricanes to Crime: Overcome Real-world Challenges with This All-flash Data Platform by Blog Home Summary Businesses today encounter many challenges. Pure Storage, an all-flash data platform, delivers the speed, performance, and reliability they need to help them tackle these hurdles and achieve their objectives. Most people think that talking about data storage is as exciting as watching paint dry.

Advertisement
Strengthen your operations with the Supply Chain Resilience Checklist. This practical, easy-to-use tool helps your organization prepare for disruptions and ensure long-term continuity in an unpredictable world. Why Download: Identify and assess critical supply chain risks Ask the right questions to evaluate vendor preparedness Implement effective strategies to reduce vulnerabilities Improve communication, transparency, and coordination across your network What You’ll Learn: How to evaluate and m

PagerDuty
SEPTEMBER 11, 2024
In an era where efficiency and smart technology integration are key, 71% of technical leaders report their companies are expanding their investments in artificial intelligence (AI) and machine learning (ML) this year. With the sheer volume of data coming into the enterprise and the need for timely response, monitoring every incoming alert around the clock is impractical, and human vigilance alone is too imprecise.
Continuity Professional Pulse brings together the best content for business continuity professionals from the widest variety of industry thought leaders.

Pure Storage
SEPTEMBER 11, 2024
Rclone vs. Rsync by Blog Home Summary Rclone and rsync are command-line tools. Rclone is designed for copying files between cloud servers and a different server or workstation, while rsync offers more advanced features for file synchronization. It’s common for administrators to synchronize files between servers, and rclone and rsync are two command-line tools used to create backups or keep files updated across multiple servers.
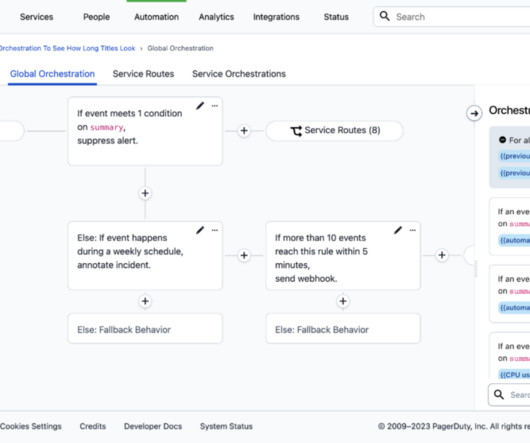
PagerDuty
SEPTEMBER 11, 2024
In an era where efficiency and smart technology integration are key, 71% of technical leaders report their companies are expanding their investments in artificial intelligence (AI) and machine learning (ML) this year. With the sheer volume of data coming into the enterprise and the need for timely response, monitoring every incoming alert around the clock is impractical, and human vigilance alone is too imprecise.

The Rand Blog
SEPTEMBER 11, 2024
Ukraine's Kursk offensive has the potential to positively influence Western perceptions, sustain funding and material support for Ukraine, and degrade Russian domestic support for the war. This strategic gamble in the information space might pay off.
Let's personalize your content