Disaster Recovery (DR) Architecture on AWS, Part II: Backup and Restore with Rapid Recovery
AWS Disaster Recovery
APRIL 26, 2021
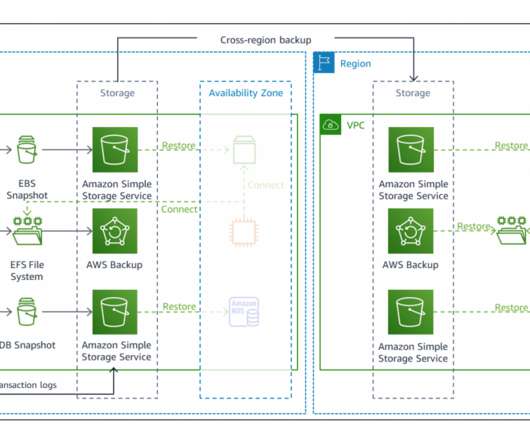
In a previous blog post , I introduced you to four strategies for disaster recovery (DR) on AWS. These strategies enable you to prepare for and recover from a disaster. Figure 6 shows that you can use AWS Backup to restore data in the recovery Region (in this case, for an EBS volume). Related information.











Let's personalize your content