Top 5 Tips for Cybersecurity Month
Zerto
OCTOBER 10, 2023
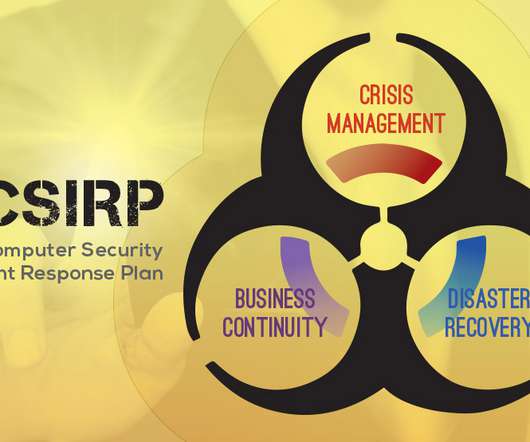
We find ourselves at the start of Cybersecurity Month, a timely reminder of the critical need to fortify your digital defense. Zerto, a Hewlett Packard Enterprise company, has five essential cybersecurity tips to help shield you from threats beyond the breach. The post Top 5 Tips for Cybersecurity Month appeared first on Zerto.





























Let's personalize your content