An Introduction to FFIEC: BCM’s Gold Standard
MHA Consulting
MARCH 23, 2023
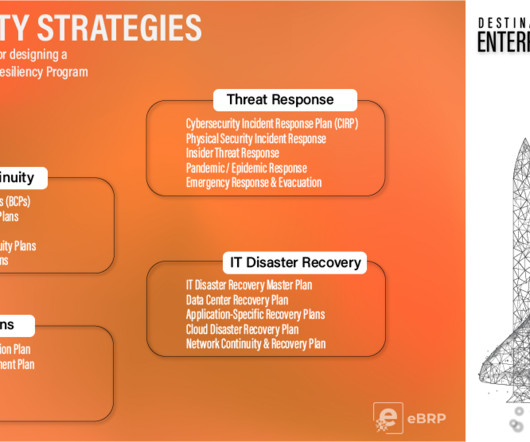
It is also comprehensive, covering all phases of the BCM program lifecycle, including risk assessment, business impact analysis, crisis management, cyber response, strategy development, plan development, testing, and maintenance. They should pick a standard and try to align with it, but it probably shouldn’t be FFIEC.
















Let's personalize your content