Planning to Reduce Crisis Overload
Bernstein Crisis Management
JUNE 26, 2023
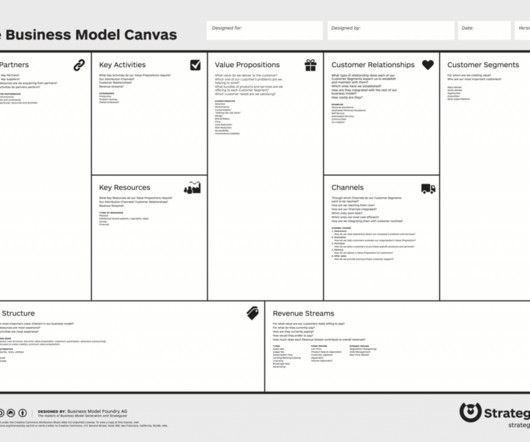
Planning to Reduce Crisis Overload Image Source: FreeImages In today’s fast-paced world, organizations face a multitude of potential crises that can disrupt their operations and reputation, and the sheer volume and variety of these crises can often lead to a sense of uncertainty.















Let's personalize your content