Chart a course for Operational Excellence with PagerDuty’s Operational Maturity Model by Alex Quintana
PagerDuty
APRIL 30, 2024
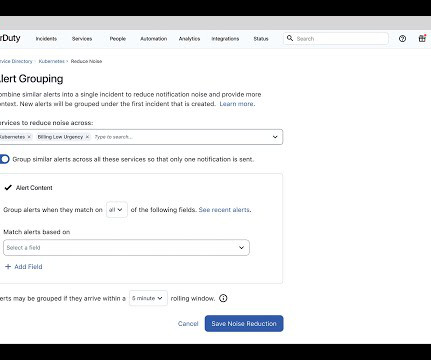
A top priority for many technical leaders is improving the performance and efficiency of their teams to maximize results and minimize costs. Why maturity matters is evident: it enables organizations to benchmark themselves against best practices, visualize their future state, and track the impact of their investments.
















Let's personalize your content