Disaster Insurance Article
Recovery Diva
JUNE 21, 2023
From HSNW: Why Insurance Companies Are Pulling Out of California and Florida, and How to Fix Some of the Underlying Problems. Author is Prof. Melanie Gall of ASU.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Recovery Diva
JUNE 21, 2023
From HSNW: Why Insurance Companies Are Pulling Out of California and Florida, and How to Fix Some of the Underlying Problems. Author is Prof. Melanie Gall of ASU.

LogisManager
MARCH 7, 2024
How Insurance Companies Can Align with the NAIC 2024 Strategic Priorities using ERM Last Updated: March 7, 2024 What are the NAIC Strategic Priorities for 2024? The National Association of Insurance Commissioners (NAIC) is the U.S. standard-setting and regulatory support organization for the state-based insurance regulatory system.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Scott R. Davis
APRIL 24, 2023
Cyber insurance policy insurers are following suit with new multi-page questionnaires outlining what your potential risk is to determine your coverages and premium or in some cases now the denial of your coverage.

Chisel AI
SEPTEMBER 22, 2021
“Data is the lifeblood of insurance companies. Insurance companies compete on analytics and algorithms, and they compete on experiences. This is our equivalent of that physical capital that Tesla has to invest in.

Security Industry Association
SEPTEMBER 7, 2023
Intego’s protection plan liabilities are 100% insured and backed by an AM Best A-Rated insurance carrier. The views and opinions expressed in guest posts and/or profiles are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association.

Pure Storage
DECEMBER 17, 2024
Also, cyber insurance premiums have risen dramatically as insurers face increasing claims, further straining budgets. Note that authorities often advise against paying ransoms, as it encourages further attacks and doesnt guarantee data recovery. Businesses sometimes spend upwards of $1.4

everbridge
MARCH 6, 2025
Operational resilience has become a defining priority for organizations in sectors like finance and insurance, especially in the UK and Europe. Aligning with regulatory expectations Global regulatory frameworks increasingly demand that organizations define and maintain impact tolerances to demonstrate operational resilience.

LAN Infotech
FEBRUARY 13, 2022
What’s more, ransomware uses a TOR browser that makes it difficult for law enforcement authorities to locate ransom websites on the dark web. Even if the authorities start tracing a wallet, cybercriminals use a bitcoin mixer to make it even harder to trace the payment. Insurance carrier. Legal team.

Pure Storage
APRIL 17, 2024
If a ransomware event happens, payer organizations can’t process authorizations, check eligibility for benefits, and often cannot connect with their providers or members. SafeMode provides an immutable copy of data that cannot be deleted unless the authorized personnel at a customer site call Pure directly.
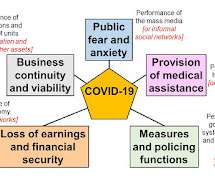
Emergency Planning
MARCH 11, 2020
In the wake of the WHO report, Professor Ziad Abdeen of the Palestinian Health Authority said about pandemics: "My task is to tell you things you don't want to know, and ask you to spend money you haven't got on something you don't think will happen."

Pure Storage
MARCH 21, 2022
Responsibilities of the communications role can include writing and sending internal and external communications about the incident, as well as contacting critical partners, authorities, external tech vendors, and affected customers with updates about remedial action being taken. Other Contacts to Know.

Pure Storage
AUGUST 4, 2021
With high-dollar insurance policies and the anonymity of cryptocurrencies, it’s more lucrative than ever. With firsthand experience, the authors explain the full life cycle of a ransomware attack so you can design a top-to-bottom response policy that guides you through each phase. How hackers identify ideal targets.

Pure Storage
MARCH 29, 2024
It has been republished with permission from the author. They will often try to discover cybersecurity insurance limits, critical operations your organization is running, and where and to whom services are provided, all in an effort to understand where an attack can do the worst damage.

Emergency Planning
APRIL 5, 2019
Consider this exchange between the authors of Lord of the Flies and For Whom the Bell Tolls. "He I have used it to shoot down both published and aspiring authors. that') failure to recognise the plural form in Latin derivatives inadvertent legalese - ‘insurance policy’ prose writing a clause as if it were a sentence.

Prism International
JUNE 14, 2023
A shredding company may have the right to pursue lost income from an at-fault driver and the at-fault driver’s insurance company after an accident. Insurance claims: The shredding company should consider filing a claim with the at-fault driver’s insurance company right away.

Pure Storage
FEBRUARY 28, 2022
This is because: The authorities or investigators may confiscate or quarantine equipment. Insurers may not let you use it. Immediately following a breach or event , you should consider your existing environment closed for business until further notice. Don’t assume you can salvage even the uncompromised functions.

NexusTek
OCTOBER 25, 2023
Penetration testing: This is an authorized, simulated attack on a company’s IT systems, which helps it to identify existing vulnerabilities. Cyber insurance: Such policies help to cover costs related to cyber incidents and indicate that a third party is paying attention to cyber risk management.

Security Industry Association
SEPTEMBER 9, 2022
Venues that support large public gatherings tend to be unprepared for a drone event and have even less authority to do something proactive. Additionally, business owners who do host the public are in a high-risk environment, while insurance companies wrestle with the appropriate level and terms for coverage.

Pure Storage
JUNE 14, 2023
That means that any affected array flagged for forensic investigation by insurance or law enforcement cannot be used and needs to be left alone. Traditionally this involves multiple parties to be on the same call to authorize these changes. Without the data storage infrastructure to get systems back up and running, you’re stuck. “By

Pure Storage
DECEMBER 6, 2021
Continue forensics efforts and work in tandem with the proper authorities, your cyber insurance provider, and any regulatory agencies. The planning should also include critical infrastructures such as Active Directory and DNS. Without these, other business applications may not come back online or function correctly.

Pure Storage
AUGUST 2, 2021
Contacts within local offices of law enforcement authorities such as the FBI in the United States may also serve useful. Also, include cyber insurance providers that can explain coverages and limitations. Also critical: preparing an external communications plan for working with the media, regulators, and legal teams.

Marketpoint Recall
JUNE 14, 2018
Your finance team are there to ensure the right insurance is purchased and to provide the documentation that the regulatory authorities require throughout a recall. Messaging should be checked to ensure they are compliant with authority guidelines and to ensure that false promises are not being made. Who should be in it?

Fusion Risk Management
SEPTEMBER 12, 2022
Ability to Procure Cyber Insurance. According to an article in Insurance Business America , the cyber insurance market started to harden in 2020 after a surge in ransomware events. Fusion’s solutions serve as a data hub for risk and resiliency, enabling you to : .

Risk Management Monitor
NOVEMBER 11, 2021
In one of the afternoon’s sessions, “Identify and Solve Any Organizational DEI Issue In One Hour,” presenter Layne Kertamus, professional in residence of risk management and insurance at Utah Valley University, explored “new ways to talk about what needs to be said, and what needs to be listened to.”.

Disaster Recovery Journal
AUGUST 5, 2020
Mintzberg, a doctoral professor of management at McGill University and author, considers business strategy as an organizational perspective of the business environment. The firm had an advantage in understanding the legal frustrations surrounding insurance claims, city investigations, and client services.

Disaster Recovery Journal
AUGUST 5, 2020
Mintzberg, a doctoral professor of management at McGill University and author, considers business strategy as an organizational perspective of the business environment. The firm had an advantage in understanding the legal frustrations surrounding insurance claims, city investigations, and client services.

everbridge
OCTOBER 7, 2024
Operational Resilience Regulations issued by the UK Financial Conduct Authority and the Prudential Regulatory Authority , effective March 31, 2022, set requirements for financial and investment firms to maintain a level of service to clients in the event of an incident. But is it enough?

Solutions Review
SEPTEMBER 9, 2021
Our editors selected the best risk management software based on each solution’s Authority Score; a meta-analysis of real user sentiment through the web’s most trusted business software review sites and our own proprietary five-point inclusion criteria.

Prism International
JULY 26, 2019
As Earl Nightingale, author of “The Strangest Secret,” said, “You become what you think about all day long.” This industry is about security and insurance, not just shredding. Having a negative attitude makes you a less likeable and approachable salesperson. This is evident whether it’s negative or positive thoughts. It’s like a virus.

Fusion Risk Management
AUGUST 12, 2024
The Third-Party Threat There seems to have been a lot of confusion around how to classify this incident; some see it as a digital or cyber issue, attempting to claim on their cyber insurance. 13 It speaks to the fact that third parties and Operations, Security, and IT teams are now all intrinsically linked. 3 billion 12.

MHA Consulting
MARCH 14, 2024
It helps organizations reduce risk, outages, impacts, and costs, such as insurance costs. They also understand how an effective ERM program can be leveraged in discussions with insurers to reduce insurance costs and increase coverage. ERM provides a framework for doing this in a systematic, results-oriented fashion.

MHA Consulting
MARCH 21, 2024
A company called Change Healthcare, which is the largest electronic clearinghouse for medical insurance payments in the country, was struck by hackers who stole patient data and encrypted company files, demanding payment to unlock them. Data breaches generally do not affect day-to-day operations.
Security Industry Association
AUGUST 4, 2022
The views and opinions expressed in guest posts and/or profiles/Q&As are those of the authors or sources and do not necessarily reflect the official policy or position of the Security Industry Association. Then there are advocacy, outreach, national campaigns, etc.

Security Industry Association
SEPTEMBER 20, 2022
Last week the Department of Homeland Security (DHS) announced a joint effort between the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Emergency Management Agency (FEMA) to provide new cybersecurity grants authorized and funded under the Bipartisan Infrastructure Law.

Advancing Analytics
AUGUST 26, 2021
Besides that, the financial industry is a vast sector that includes banks, building societies, e-money institutions, mortgage companies, investment banking, credit unions, insurance and pension companies. Interestingly, the insurance sector has 100% live machine learning applications in use. Fraud Detection.

Security Industry Association
OCTOBER 7, 2024
Furthermore, following an incident, utilities may face surging insurance premiums, legal liabilities, reputational damage, and regulatory hurdles, which could entail penalties and the need for corrective measures to prevent future occurrences. Protecting the vast U.S.

Pure Storage
OCTOBER 27, 2021
Get in touch with critical partners and authorities. If you’re working with the media, regulators, and legal teams after an attack, it’s helpful to maintain an updated list of contacts within local offices of law enforcement authorities such as the FBI in the United States.

Security Industry Association
SEPTEMBER 4, 2024
Access control systems will no longer serve as the sole automated authority on identification and permissions. Many only recognize its importance when it’s too late, much like the reactionary nature of insurance. Culture: There is a widespread reluctance to invest proactively in security.

Solutions Review
SEPTEMBER 14, 2021
This is what I call risk management 1 – risk management for external stakeholders (Board, auditors, regulators, government, credit rating agencies, insurance companies and banks). None of these things have anything to do with proper risk management.

Plan B Consulting
APRIL 2, 2024
According to Lloyd’s, this event might be the biggest ever marine loss in the history of the insurance industry as the event was a ‘fully insured risk event’, meaning that the Francis Scott Key Bridge, the ship, the vessel’s cargo, and the port, were all covered.

Security Industry Association
JANUARY 3, 2023
The simple answer is that we need delegated authorities backed by regulation or law that help to incentivize action. Form an official public/private CUAS task force with decision authority. The dire requirement for a public/private task force is at a critical juncture.

Business Resilience Decoded
DECEMBER 16, 2021
Few are prepared for the stress that occurs when a hacker encrypts their data and their insurance company tells them they won’t pay. He is also the author of “No Safe Harbor: The Inside Truth About Cybercrime and How to Protect Your Business.”

Business Resilience Decoded
DECEMBER 16, 2021
Few are prepared for the stress that occurs when a hacker encrypts their data and their insurance company tells them they won’t pay. He is also the author of “No Safe Harbor: The Inside Truth About Cybercrime and How to Protect Your Business.”

Solutions Review
SEPTEMBER 27, 2021
Our editors selected the best governance, risk, and compliance software based on each solution’s Authority Score; a meta-analysis of real user sentiment through the web’s most trusted business software review sites, and our own proprietary five-point inclusion criteria.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content