Pandemic Planning: What is a Pandemic Operating Regime, and do I need one?
Plan B Consulting
JANUARY 30, 2020
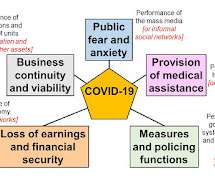
Following the spread of Coronavirus throughout China and surrounding countries, Charlie introduces the idea of a Pandemic Operating Regime and why you should develop one. I want to introduce the idea of a Pandemic Operating Regime (POR), explain what it is and why I suggest that you develop one.























Let's personalize your content