Webinar: The Importance of Multi-factor Authentication (MFA)
Disaster Zone
AUGUST 15, 2022
It is another step—keeping you more secure.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Disaster Zone
AUGUST 15, 2022
It is another step—keeping you more secure.

Citrix
JUNE 7, 2023
It is universally agreed that ‘authentication and login security’ is critical to ensuring access and network security into an organization’s assets. While login security is critical and constantly evolving, it’s important to manage this whilst ensuring end user productivity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Citrix
MAY 9, 2022
However, all hybrid employees need reliable and … The post Citrix Features Explained: Adaptive authentication and access in Citrix Secure Private Access first appeared on Citrix Blogs.

Security Industry Association
DECEMBER 12, 2024
Artificial intelligence (AI) has had a big impact on the video surveillance and security sectors over the past year automating tasks such as threat detection, object recognition and predictive analytics with better accuracy than ever. These advancements have been essential tools to help empower security teams.

Citrix
OCTOBER 5, 2022
Authentication and authorization are essential processes of identity and access management. While the terms are often used interchangeably, authentication and authorization fill different functions. The Main Differences first appeared on Citrix Blogs.

Citrix
AUGUST 4, 2022
Many organizations also have … The post Why should you evolve your multi-factor authentication to adaptive authentication? Distributed workforces and online users compound the challenge since they often need remote access to critical apps and data. first appeared on Citrix Blogs.

Citrix
NOVEMBER 4, 2021
One of the most effective … The post Biometrics authentication into Citrix Workspace with TrustKey FIDO2 Security Keys first appeared on Citrix Blogs. With the pandemic, organizations have experienced an increase in hacking attacks, resulting in immense loss and damage for many businesses.

Pure Storage
FEBRUARY 14, 2024
New Pure1 Mobile App Features Enhance Security and Storage Optimization by Pure Storage Blog Introducing the latest evolution of the Pure1 ® Mobile Application! This feature streamlines the approval process, ensuring seamless collaboration and enhanced security for your storage environment. Figure 4: Biometric authentication.

Citrix
JUNE 1, 2022
This diversity has created a complex landscape of devices … The post Introducing Citrix Adaptive Authentication first appeared on Citrix Blogs. The way people work has changed over the last two years, and even as we see more people returning to the office, remote, hybrid, and mobile workstyles are here to stay.

Citrix
SEPTEMBER 1, 2022
Citrix has crafted new signatures and has updated its Citrix Web App Firewall signature file to help customers mitigate the recent authentication bypass vulnerability in multiple versions of Atlassian Confluence app (versions prior to 2.7.38 and 3.0.5).

Security Industry Association
JULY 27, 2021
Meeting the security challenges of modern office environments is a complex and long-standing issue for many organizations. However, with greater flexibility come increasing security demands – both in and outside the office. Employers and employees alike are more conscious about privacy and security than ever before.

Erwood Group
MAY 20, 2024
Enable Two-Factor Authentication (2FA) to Add an Extra Layer of Security to Your Accounts Enable Two-Factor Authentication (2FA) to Add an Extra Layer of Security to Your Accounts Securing online accounts has never been more critical. This is where Two-Factor Authentication (2FA) comes into play.

Citrix
JUNE 16, 2022
Citrix Secure Private Access?????????????????. ??????CitrixCloud?????????ID???????????????????????????????????????????????????????. Citrix Secure Private Access???Web????SaaS????????????????????PC???????????????????????????????????????????????????????????????????????????????????. Workspace????????????????????????????????????????????2022?6?1????????????????????????Citrix

Security Industry Association
APRIL 7, 2022
Access control applications, including touchless authentication, mobile credentials, and distancing analytics, can help businesses create a secure and healthy working environment for all employees. Key card access controls are ubiquitous in workplaces, securing facilities and employees with little friction or complication.

Citrix
MAY 12, 2022
But today the average business relies on 88 different apps , creating a larger-than-ever attack surface … The post Citrix Features Explained: Increase app security with Citrix Secure Private Access first appeared on Citrix Blogs.

Zerto
JANUARY 4, 2024
Thales, with its CipherTrust Data Security Platform and Luna Hardware Security Modules (HSMs), partners with HPE and Zerto, a Hewlett Packard Enterprise company, to provide enterprise data protection solutions for HPE GreenLake customers, with centralized key management and encryption for on-premises, at the edge, cloud, and hybrid environments.

Citrix
AUGUST 11, 2022
The reality of today’s fast-paced, increasingly remote work environment positions your business as vulnerable to security breaches. … The post Seven principles of the zero trust security model first appeared on Citrix Blogs. Related Stories Why should you evolve your multi-factor authentication to adaptive authentication?

Citrix
JUNE 7, 2023
It is universally agreed that ‘authentication and login security’ is critical to ensuring access and network security into an organization’s assets. While login security is critical and constantly evolving, it’s important to manage this whilst ensuring end user productivity.

Citrix
JANUARY 30, 2023
That’s why we are excited to announce general availability … The post Citrix Endpoint Management now supports NetScaler advanced authentication policies (nFactor) first appeared on Citrix Blogs. Related Stories Citrix Endpoint Management now supports IdP enrollment for MAM Citrix Endpoint Management is back by popular demand!

Disaster Zone Podcast
FEBRUARY 23, 2021
This podcast is an interview with Jeff Kirchick, author of the book Authentic Selling, How to use the Principles of Sales in Everyday Life. In this podcast we discuss what it takes to be authentic and how incorporating listening and being empathetic can help you interact more effectively with others.

Online Computers
NOVEMBER 23, 2021
An organization’s readiness to respond to or recover from any IT security incident determines whether it will survive or shut down after a cyberattack. Cybercriminals are taking advantage of distributed work environments and expanding their targets, making it tough for IT teams and business owners to secure all potential vulnerabilities.

Citrix
AUGUST 15, 2022
This suggests the … The post Citrix Features Explained: Improving end-user security with Citrix Secure Private Access first appeared on Citrix Blogs. Related Stories Seven principles of the zero trust security model Why should you evolve your multi-factor authentication to adaptive authentication?

Pure Storage
DECEMBER 18, 2023
7 Challenges with Applying AI to Data Security—and the Real Way to Solve Them by Pure Storage Blog As AI makes headlines and augments the way we work, there’s one area to be cautiously optimistic about: cybersecurity. There isn’t a silver bullet in security, but AI’s false sense of security can be risky. Can it lend a hand?
Pure Storage
AUGUST 23, 2023
How To Use SSH Public Key Authentication by Pure Storage Blog Instead of using the same key to decrypt and encrypt connections, public key encryption uses a public and private key. This system improves security of Secure Shell (SSH) connections when administrators remotely connect to servers and workstations.

Security Industry Association
AUGUST 15, 2024
The Security Industry Association (SIA) has named two recipients for the 2024 Denis R. The winners for the 2024 Hébert Scholarship are Mariana Lima, data privacy analyst, legal, at dormakaba USA, and Samuel Silvamolina, electronic security systems engineer at M.C. Samuel Silvamolina is an electronic security systems engineer at M.C.

Citrix
MAY 19, 2022
You want your hybrid workers to be able to easily browse the internet for whatever insights and resources they need to do their best work — but … The post Citrix Features Explained: Browser security in Citrix Secure Private Access first appeared on Citrix Blogs.

Citrix
OCTOBER 11, 2022
VPNs have long been a security standard for secure access to corporate applications. Organizations began using VPN services at a time when the digital world was far less complex, however, and today, VPNs are far from secure. This blog post … The post Remote Access Without VPN: Is It Secure?

Security Industry Association
OCTOBER 6, 2022
The Security Industry Association (SIA) reiterates its commitment to cybersecurity as the 2022 Cybersecurity Awareness Month – observed every October – begins. Just like with physical security, real cybersecurity is achieved through diligent efforts from people to create and execute on processes,” said SIA CEO Don Erickson.

Solutions Review
JUNE 16, 2023
In this feature, SANS Institute Dean of Research Dr. Johannes Ullrich explains the critical role of safe and secure backup system storage. Due to poor password hygiene or the absence of two-factor authentication, these backup systems can be easy targets for threat actors to utilize as attack vectors against protected systems.

Security Industry Association
MARCH 23, 2022
Over the past few years, the Security Industry Association’s (SIA’s) Open Supervised Device Protocol (OSDP) standard – developed by SIA to improve interoperability among access control and security products – has been steadily gaining momentum as the standard for secure access control. Why Specify or Adopt OSDP?

Citrix
NOVEMBER 16, 2021
Citrix customers traditionally had to publish a virtual browser on Citrix Virtual Apps and Desktops or rely on a local browser with minimal authentication security to enable secure access to internal web and SaaS apps.

Security Industry Association
SEPTEMBER 14, 2023
New Security Industry Association (SIA) member Wicket offers computer vision technology for facial ticketing, access control, frictionless payment and credentialing. SIA spoke with Jeff Boehm, chief marketing officer at Wicket, about the company, the security industry and working with SIA. Tell us the story of your company.

Citrix
JUNE 9, 2022
Citrix has been in the business of delivering secure remote work through its digital workspace solutions for more than three decades. Related Stories ZTNA Vendors: What to look for Introducing Citrix Adaptive Authentication VDI best practices and tips to support remote work.

Pure Storage
SEPTEMBER 16, 2021
With any ransomware attack or security event, there’s going to be a before, a during, and an after. 5 Ways to Close Security Gaps Before an Attack. Implement multi-factor authentication and admin credential vaulting for all systems. It’s not just enough to maintain security logs. Perform good data hygiene on systems.
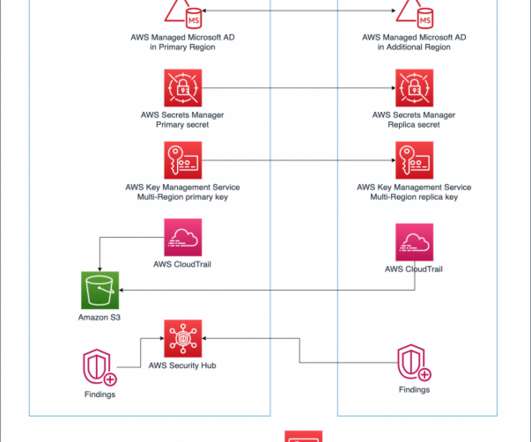
AWS Disaster Recovery
DECEMBER 8, 2021
In Part 1, we’ll build a foundation with AWS security, networking, and compute services. Ensuring security, identity, and compliance. Creating a security foundation starts with proper authentication, authorization, and accounting to implement the principle of least privilege. Considerations before getting started.

Security Industry Association
MARCH 21, 2022
New Security Industry Association (SIA) member Allthenticate provides an all-in-one access control and authentication solution for companies that is designed to be cost-effective, easy to use and secure. What solutions/services does your business offer in the security industry? Tell us the story of your company.

NexusTek
JULY 7, 2021
Cyber Security: 8 Steps to Cyber Resilience. You’ve heard of cyber security, but have you heard of cyber resiliency? Both cyber security and cyber resilience are essential to protecting the bottom line, productivity, and brand reputation of a business. READ TIME: 4 MIN. July 7, 2021. No cybersecurity solution is infallible.

Pure Storage
JULY 14, 2022
According to Cybersecurity Insiders’ 2022 Cloud Security Report : . Nearly half (47%) of organizations cite “loss of visibility and control” as one of their biggest challenges around securing multi-cloud environments. . In part 2 of our three-part cloud data security blog series, we discussed the issue of complexity.

Security Industry Association
FEBRUARY 27, 2023
The globally recognized program will honor innovative women guiding the biometrics and security industry during the 2023 SIA GovSummit. The recipients of this year’s Women in Biometrics Awards will be honored at the 2023 SIA GovSummit , SIA’s annual government security conference. Learn more and register to attend here.

NexusTek
APRIL 19, 2023
READ TIME: 4 MIN April 19, 2023 Money at Risk: Finance & Data Security in the Digital Age Across industries, providing customers with superior experience is essential for success. Getting a sense that their bank, lender, or investment firm has weak security can drive customers to close their accounts and switch to a competitor.
Pure Storage
DECEMBER 7, 2023
by Pure Storage Blog When you have multiple operating systems and devices connected together, you need a centralized directory service to control authentication and authorization. In addition to access control, administrators can integrate two-factor authentication (2FA) and single sign-on (SSO) with directory services for better security.

Citrix
NOVEMBER 8, 2021
No matter how good software developers … The post Take a proactive approach to CVE-related security for your Citrix ADC first appeared on Citrix Blogs. Did you know there’s an attack by a hacker every 39 seconds and that hackers steal 75 data records every second?

Citrix
MAY 9, 2022
Certain operating systems such as Windows Server 2019 and Windows 10 version 1809 are, by default, not vulnerable … The post Guidance for reducing HTTP protocol RCE security vulnerability risk with Citrix Web App Firewall (CVE-2022-21907) first appeared on Citrix Blogs.

Security Industry Association
MAY 18, 2022
Gena Alexa, Amanda Conley, Delia McGarry, Diane Stephens and Bobby Varma will be honored for their leadership and contributions in biometrics and security at the 2022 SIA GovSummit. The 2022 awardees, who will be honored at the 2022 SIA GovSummit , SIA’s annual government security conference, are: Gena Alexa, CEO and Founder, Dignari.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content