Unleashing a Range of Secure and Seamless Authentication Options on Citrix Workspace App
Citrix
JUNE 7, 2023
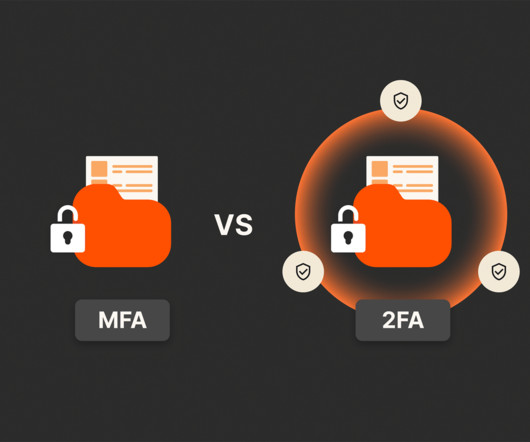
It is universally agreed that ‘authentication and login security’ is critical to ensuring access and network security into an organization’s assets. While login security is critical and constantly evolving, it’s important to manage this whilst ensuring end user productivity.















































Let's personalize your content