Cybersecurity Awareness Month 2024: Doing Our Part to #SecureOurWorld
Pure Storage
OCTOBER 1, 2024
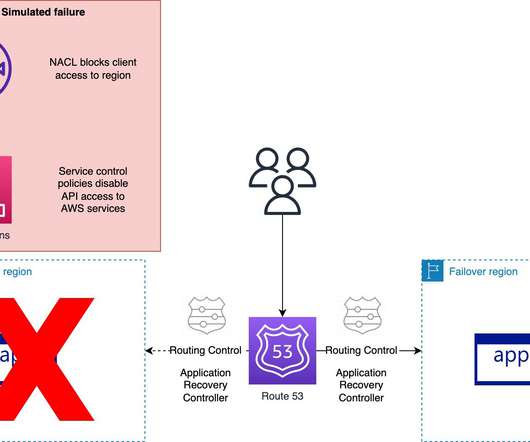
Enabling multi-factor authentication (MFA). The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) encourages security and IT teams to work together to reduce the impact of attacks and even prevent outages and permanent data loss. Learn more in “ Why Identity Is the New Network Perimeter.” NIST CSF 2.0—



















Let's personalize your content