Why Cybercriminals Are Targeting Your Backups and How to Be Prepared
Solutions Review
APRIL 7, 2025
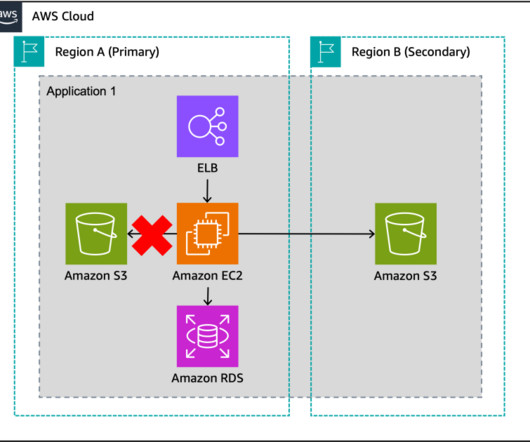
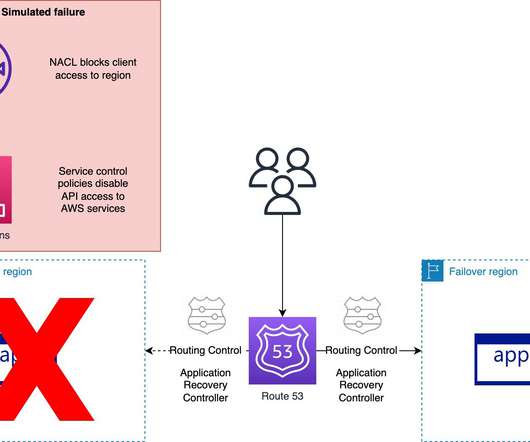
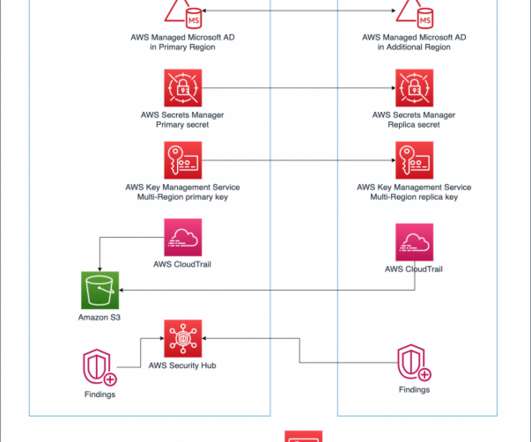
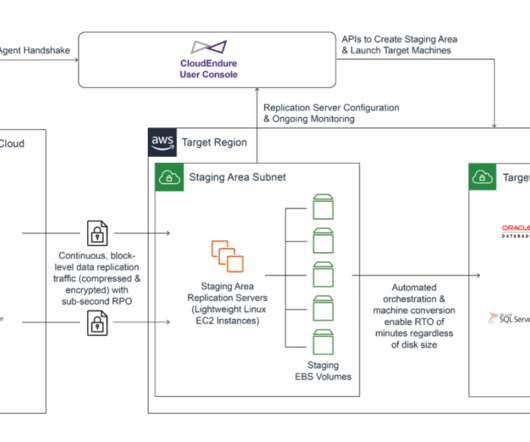
The implementation of advanced authentication methods like Multi-Factor Authentication (MFA) and the Principle of Least Privilege (POLP) on backup systems. Businesses should spread their backup infrastructure across multiple cloud providers, using distinct authentication systems and separate environmental controls.




















Let's personalize your content