Download: Separation of Duties (SoD) Checklist
LogisManager
MAY 15, 2025
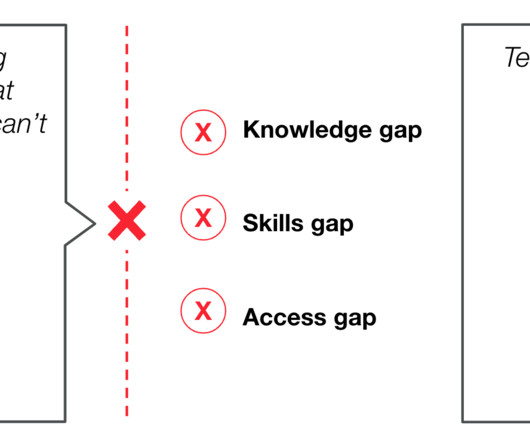
This practical guide will help you establish clear roles, monitor access, and implement controls to mitigate potential vulnerabilities. Regular Monitoring and Review: Conduct periodic audits to evaluate the effectiveness of SoD practices and make adjustments as needed. Why Adopt Separation of Duties?



























Let's personalize your content