What is COBIT? COBIT Explained
BMC
DECEMBER 5, 2024
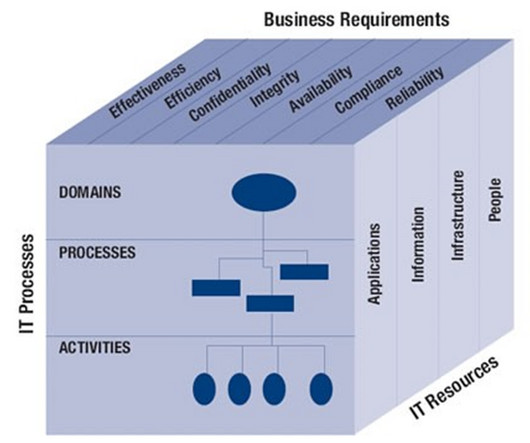
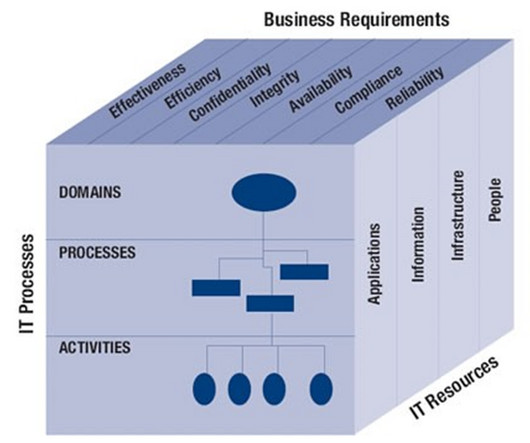
It was first introduced by the Information Systems Audit and Control Association (ISACA) in 1996, and has gone through many rounds of development since. ISACA stands for the Information Systems Audit and Control Association. These frameworks aim to make it easier for enterprises to undergo and pass regulatory audits.












































Let's personalize your content