What Is Cyber Extortion? Tips for Securing Your Data
Pure Storage
DECEMBER 17, 2024
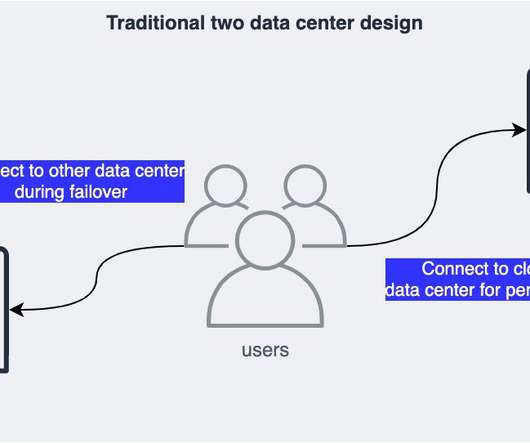
Zero trust architecture ensures a “never trust, always verify” approach to limit access and minimize potential damage from breaches. Creating one involves developing and testing a clear incident response plan for responding to cyber extortion attempts, including communication protocols and steps for recovery.






















Let's personalize your content