Cybersecurity Awareness Month 2024: Doing Our Part to #SecureOurWorld
Pure Storage
OCTOBER 1, 2024
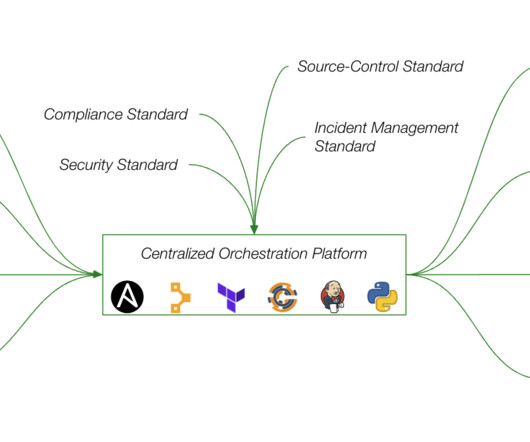
This and other security controls are aspects of zero trust architectures , which should be looked at as a journey, not a destination. The backbone of cyber resilience comes from a foundation: a data-resilient security architecture deeply integrated with tech partners who can uphold the latest standards and frameworks. Let’s dig in.















Let's personalize your content