Implementing Multi-Region Disaster Recovery Using Event-Driven Architecture
AWS Disaster Recovery
JULY 27, 2021
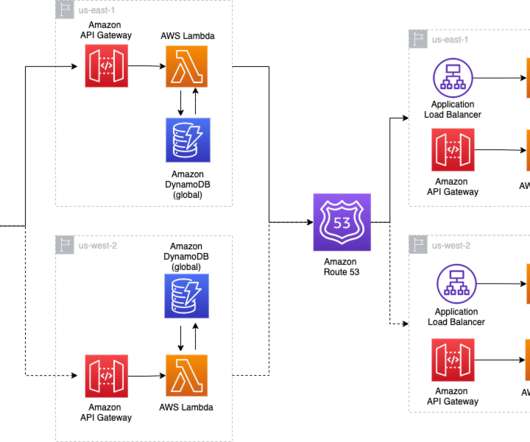
In this blog post, we share a reference architecture that uses a multi-Region active/passive strategy to implement a hot standby strategy for disaster recovery (DR). DR implementation architecture on multi-Region active/passive workloads. Fail over with event-driven serverless architecture. This keeps RTO and RPO low.






















Let's personalize your content