Why Cybercriminals Are Targeting Your Backups and How to Be Prepared
Solutions Review
APRIL 7, 2025
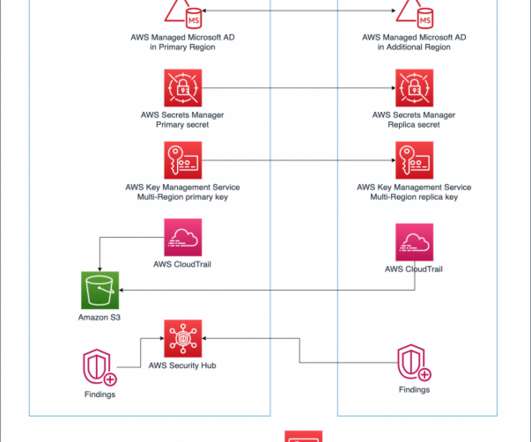
Each test generates detailed audit trails, providing both compliance documentation and security validation. Multi-Cloud Architecture A distributed backup ecosystem provides essential protection against both targeted attacks and systemic failures. Which brings us to 3.































Let's personalize your content