Software modernization: solutions, strategies, and examples.
BMC
NOVEMBER 20, 2024
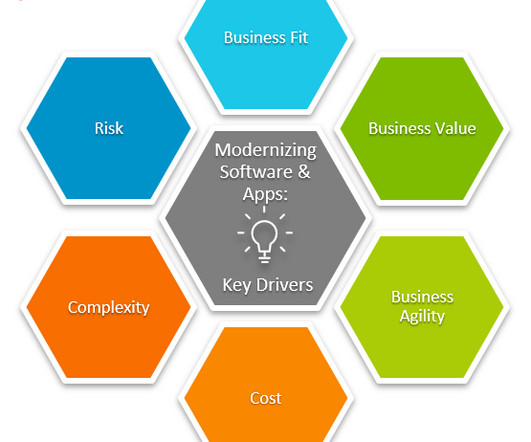
And modernizing software and applications is a critical part of any successful digital transformation. After all, legacy software applications and technologies limit your organization’s ability to enable a digital-first user experience and business operations. The Market. Digital transformation requires being proactive.















































Let's personalize your content