How an insurance company implements disaster recovery of 3-tier applications
AWS Disaster Recovery
NOVEMBER 11, 2024
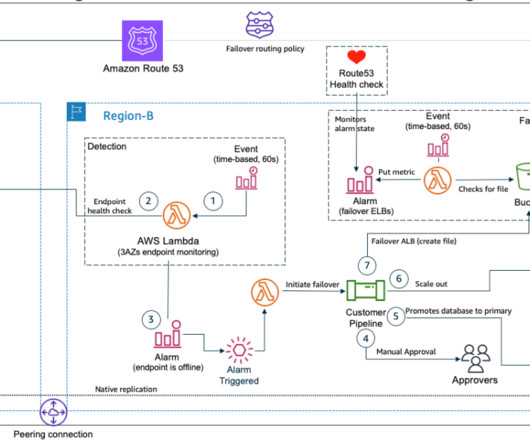
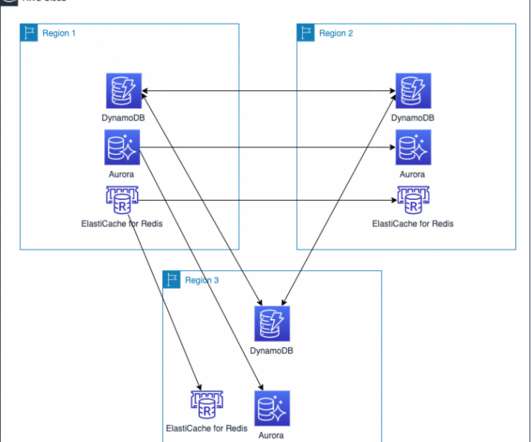
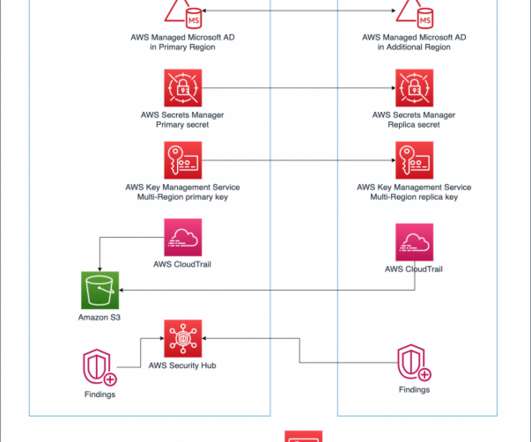
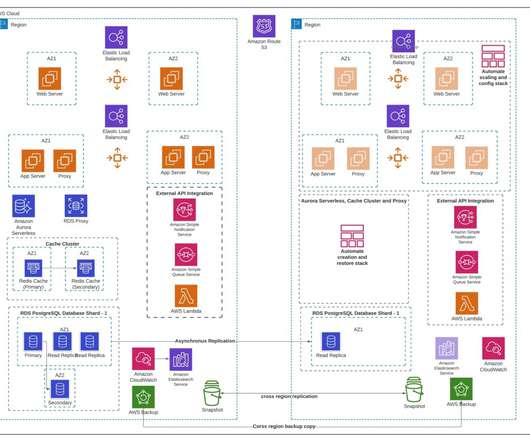
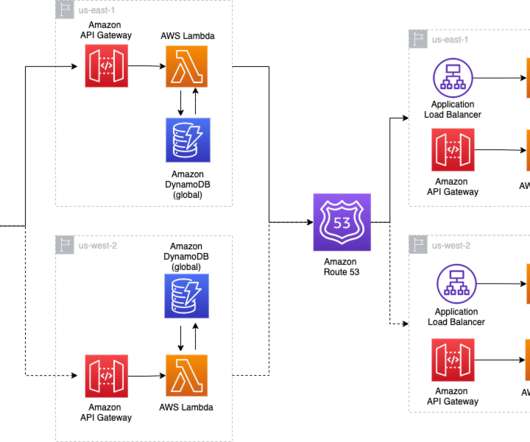
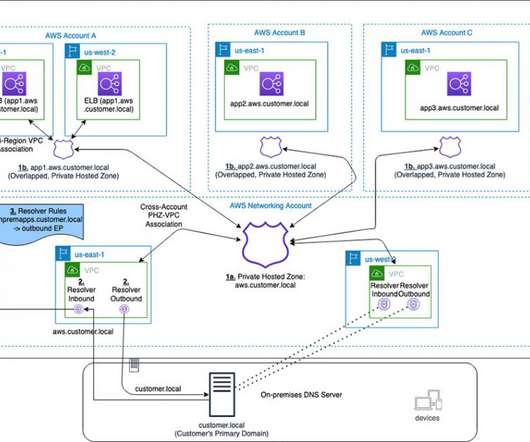
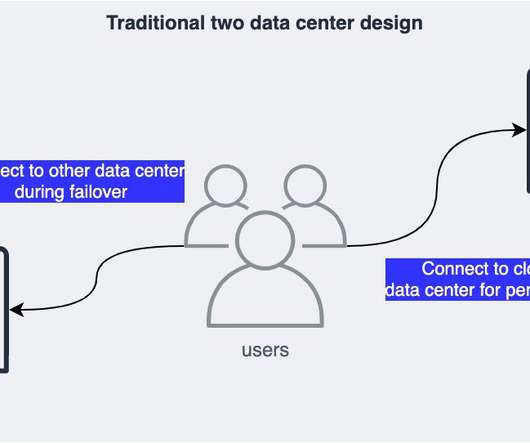
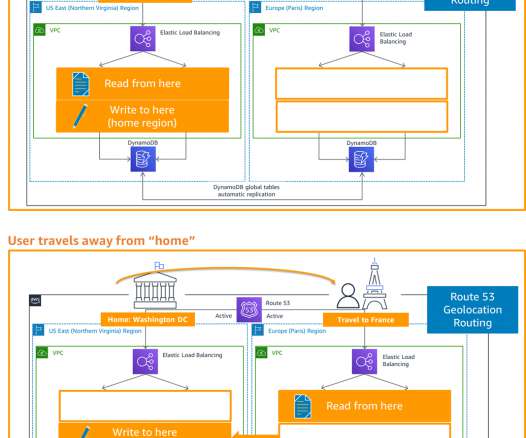
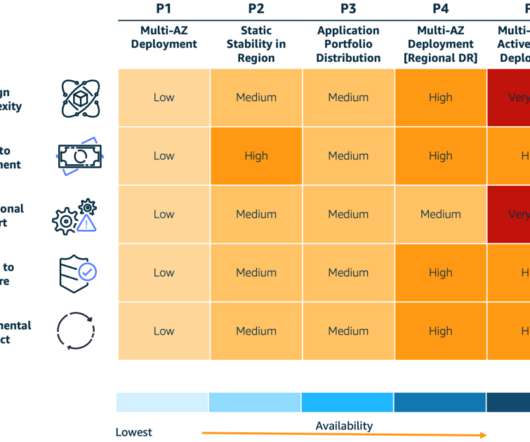
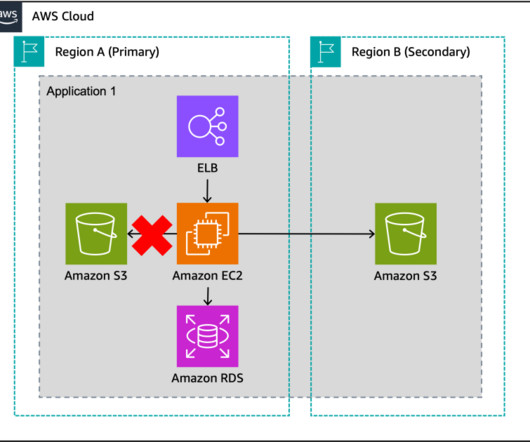
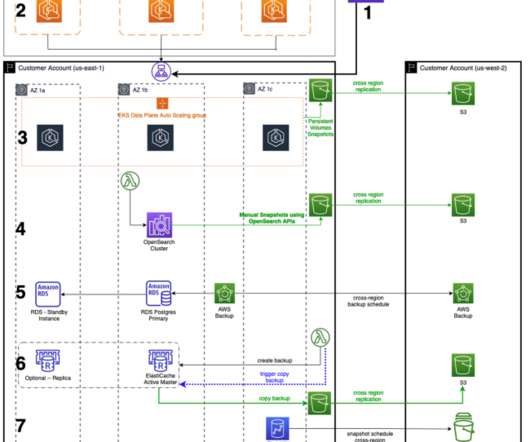
In this post, we explore how one of our customers, a US-based insurance company, uses cloud-native services to implement the disaster recovery of 3-tier applications. At this insurance company, a relevant number of critical applications are 3-tier Java or.Net applications.




































Let's personalize your content