Double trouble: When climate change and cyber crime collide
everbridge
NOVEMBER 11, 2024
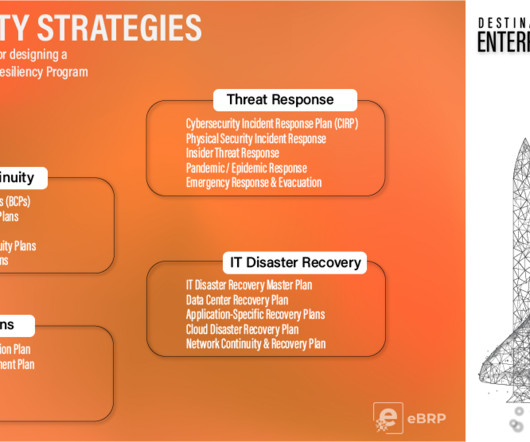
Today, many BCDR programs rely on response plans for a handful of most likely potential incidents. Preparing for the worst case scenario Beyond the BIA, risk assessment, and response plan, there are several steps an organization can take to prepare itself for a simultaneous disaster and cyber attack. Build awareness.
























Let's personalize your content