Double trouble: When climate change and cyber crime collide
everbridge
NOVEMBER 11, 2024
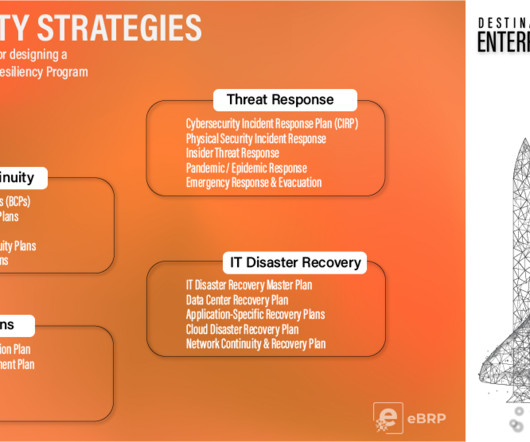
Today, many BCDR programs rely on response plans for a handful of most likely potential incidents. At the same time, organizations in disaster zones may be forced to prioritize physical recovery over cybersecurity, leaving doors open for attackers to penetrate networks or systems. Think beyond single scenario planning.















Let's personalize your content