Your Cyber Resilience Wish List for 2025—and How to Achieve It
Pure Storage
MAY 14, 2025
Watch the Webinar The post Your Cyber Resilience Wish List for 2025and How to Achieve It appeared first on Pure Storage Blog. ” Cyber Resilience, Pure and Simple Fortify your data and guarantee uninterrupted business operations. See How The Latest in Cyber Resilience Discover actionable insights and practical defense strategies.












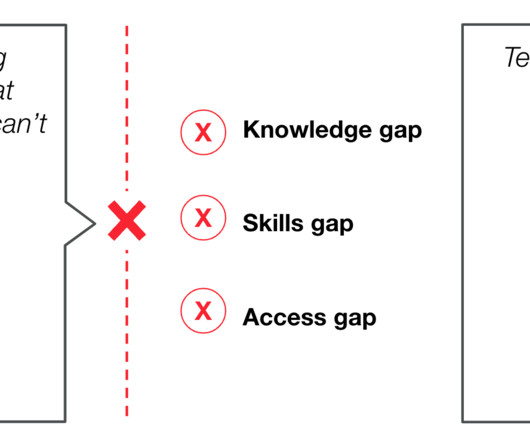







Let's personalize your content