How to Offload Your Risk to a Third Party
MHA Consulting
FEBRUARY 9, 2023
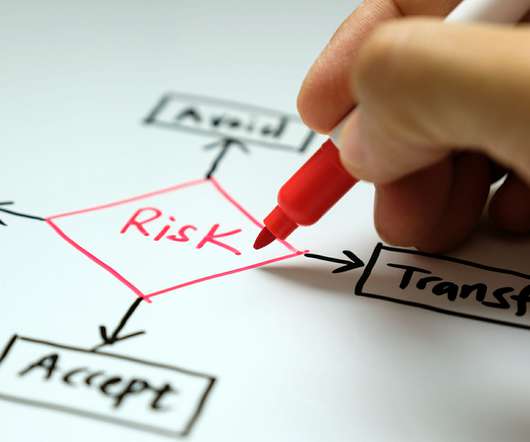
. · Risk avoidance: Altering organizational behavior to eliminate a given risk. Risk limitation: Taking measures to reduce risk, short of completely eliminating it. Incorporates a combination of the strategies of risk avoidance and risk acceptance.













Let's personalize your content