These 8 Risk Domains Are the Meat and Potatoes of Risk Management
MHA Consulting
AUGUST 3, 2023
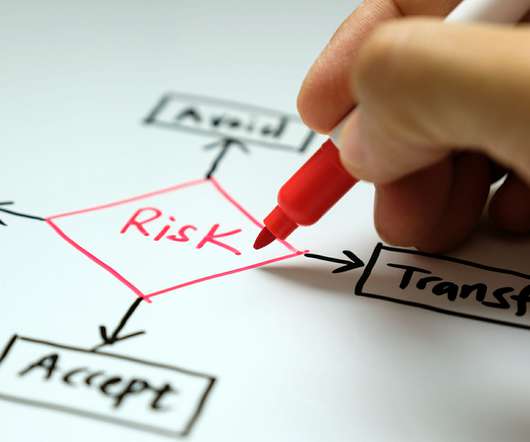
In today’s post, we’ll lay out what these domains are, reveal which ones tend to get overlooked, and explain how knowing about the domains can help business continuity professionals reduce their organizations’ risks and bolster their resilience. For more on those strategies, click here and here.)













Let's personalize your content