Risk Management Process – Part 3c: Risk Control
Zerto
AUGUST 24, 2023
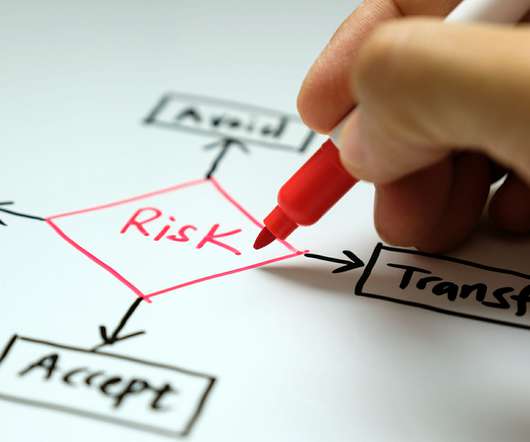
The third crucial step in risk assessment is risk control, which involves crafting effective strategies to mitigate the identified risks. There are four fundamental types of risk control: risk acceptance, risk mitigation, risk avoidance, and risk transfer.














Let's personalize your content