PagerDuty Operations Cloud Fall Launch 2023 by Inga Weizman
PagerDuty
OCTOBER 30, 2023
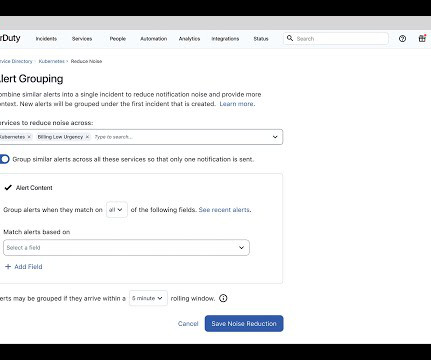
CIOs have needed to build strategies to mitigate the risk of operational failure and protect their brand’s customer experience. This democratizes automation authoring across the organization for IT operations, SRE and platform engineering teams, and lends a hand to less experienced users. Incidents will happen.












Let's personalize your content