FEMA is Not Prepared for the Next H. Katrina
Recovery Diva
JUNE 22, 2025
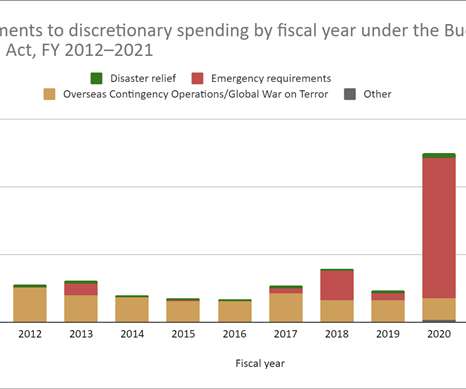
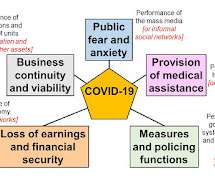
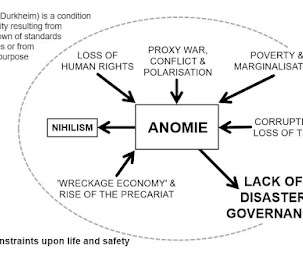
“Cuts, chaos, and climate change are converging to leave Americans more vulnerable to disaster than they were in 2005” From Yale Climate Connections: FEMA is unprepared for the next Hurricane Katrina, disaster experts warn.




















Let's personalize your content